|
Cryptome DVDs are offered by Cryptome. Donate $25 for two DVDs of the Cryptome 12-years collection of 46,000 files from June 1996 to June 2008 (~6.7 GB). Click Paypal or mail check/MO made out to John Young, 251 West 89th Street, New York, NY 10024. The collection includes all files of cryptome.org, jya.com, cartome.org, eyeball-series.org and iraq-kill-maim.org, and 23,000 (updated) pages of counter-intelligence dossiers declassified by the US Army Information and Security Command, dating from 1945 to 1985.The DVDs will be sent anywhere worldwide without extra cost. | |||
Table of Contents of main report.
FM 100-6 INFORMATION OPERATIONS
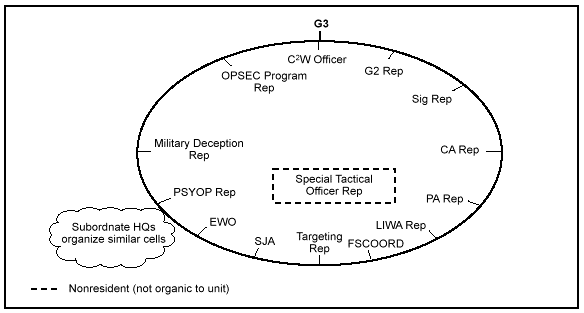
Based on the considerations of METT-T, the commander may designate an IO cell on his staff. The structure of the cell is the prerogative of the commander. It may be something as simple as periodic use of an expanded targeting cell or a more formal approach establishing a standing cell with a specifically designated membership. The IO cell is normally found at the task-force level, independently operating brigade level, or above. A notional view of the IO cell is shown in Figure D-1.
The IO cell should have representatives from the targeting cell, targeting board, joint operations and targeting coordination board, or whatever integrating process the commander uses to integrate and synchronize his resources. Each element of C2W should be represented where possible. In OOTW situations the CA representative and/or PA representative may take on more importance. In conflict and war the targeting representative may become the focus of activity. Functions of the IO cell include--
Consolidated tasking will assist in the integration and synchronization required for effective IO, including coordination with the joint IW community.
As the spectrum of engagement moves from peace to war, it may be more appropriate to stand up an IOBS. An IOBS would be appropriate at division and above and most appropriate at corps. Although the functions would be relatively the same as the IO cell, they would be much broader in scope. This type of staff organization would be best suited for deployment in the context of a campaign, as discussed in Appendix A (see Figure D-2).

As in all areas, effective IO requires soldiers to train the way they are going to fight or operate. The basic task is to train the force on IO, with an initial focus on those personnel responsible for planning and coordinating the individual elements. When our leaders and units are exposed to realistic IO elements in training, such as information distribution in OOTW, their readiness and confidence increases.When employing IO in exercises, the following considerations are important:

Effective IO first requires specific information products on the adversary's military (C2, intelligence, and capabilities), social, religious, and economic background that may have to be provided by exercise planners. The data needed to create, update, and use these products needs to be built into the exercise scenario and master scenario events list.
Secondly, the opposition force should have an IO capability consistent with the OPLAN/CONPLAN scenario that is the basis for the exercise. Realistic IO are essential to evaluating friendly IO.
Finally, consistent with the tenets of the exercise, free play of IO should be allowed by both sides. Prestructured, mechanical IO will degrade the participant's ability to gain valuable experience from the demands of mental agility and creativity that unstructured IO can provide. Senior exercise participants should allow, even welcome, the C2 chaos that effective IO can cause to the exercise participants and work through such problems.
A basic IO mission-essential task list (METL) includes tasks and subtasks. Tasks involve each IO component--operations, relevant information and intelligence, and INFOSYS. The METL enhances the objective of achieving information dominance at selected places and times during an operation. Tasks include--
-Identify the commander's IO CCIR, PIR, and high-priority targets and synchronize intelligence and information plans and military plans on a near-real-time basis.
-Establish information-linked strategic, operational, and tactical collection, fusion, and report processes (incorporating RISTA/sensor and CI/HUMINT data) to develop continuous, timely IO IPB.
-Provide IO modeling and simulation for training and evaluating performance, mission rehearsal, and decision making.
-Identify and prioritize IO EEFI.
-Maintain a continuous IO estimate of potential adversaries and/or other operational situations in support of IO situational awareness and battlefield visualization.
-Assess adversary C4I/C2W operations, strengths, and vulnerabilities continuously.
-Understand the enemy's decision-making process.
-Identify the enemy's critical IO nodes.
-Develop enemy leader personality profiles.
-Understand the enemy's decision-making doctrine, tactics, and standard operating procedures.
-Establish open-source processes to obtain, process, provide, secure, and release critical IO information, including PA, CA, governmental, and nongovernmental information within legal and policy constraints.
-Establish and maintain critical, secure, intertheater/intratheater, military communications and computer networks that support IO; for example, digitization, RCP, situational awareness, battlefield visualization, distribution, and C2 across the battle space.
-Assess friendly C2 vulnerabilities and C2-protect operations continuously and adjust to maintain C2 effectiveness.
-Achieve C2 protection in support of data integrity and infrastructure protection, IO/C2 node protection, spectrum superiority/control, and graceful degradation.
-Establish procedures to regain information dominance when it is discovered that the enemy has achieved information dominance.
-Establish C2-attack targeting and BDA and establish links to expedite dissemination of adversary information, to include timely sensor-to-shooter links.
-Attack, deny, degrade, exploit, and/or influence adversary C4I/C2W capabilities or other operations using lethal and nonlethal means.